Visitor management systems are more than just administrative tools; they are essential for safeguarding proprietary information and ensuring secure storage and everyone’s safety on site. If you want to know more about their benefits, we’ve got you covered. Let’s explore how these systems are pivotal for your business. Read our article to learn how a visitor management system can help you digitize and upgrade your business.
Why Manufacturing Needs Dedicated Visitor Management Systems
Safeguarding intellectual property and trade secrets
Visitor management systems (VMS) play a crucial role by ensuring that only authorized visitors and employees have access to a specific location at the facility. They can screen all visitors, track activity, manage entry permissions and visitor trends, and maintain a detailed log of all entries and exits.
Ensuring workforce safety and facility security
Visitor management software contributes significantly to workforce safety. These systems ensure that individuals on-site are authorized and have a legitimate purpose. As a result, this helps mitigate risks of accidents, boost security and compliance, and keep everyone safe.
Maintaining regulatory compliance
For manufacturers dealing with international traffic in arms regulations (ITAR) or adhering to International Standards Organization (ISO) protocols, it is non-negotiable to comply with strict regulations. Visitor management for manufacturing facilities helps comply with these stringent standards and provide verifiable logs and data that prove compliance with regulatory requirements.
Increasing operational productivity and efficiency
A robust visitor management system streamlines the flow of people, minimizing potential disruptions and improving overall operational efficiency. By automating visitor registration, printed badges, and hosting delivery notifications, VMS allows for a quicker, more efficient touchless check-in process. The data gathered by VMS can be analyzed to screen people and optimize their movement.

Leading Regulatory Standards for Compliance
CCPA (California Consumer Privacy Act)
In manufacturing, where data about employees and visitors is often stored and processed, compliance with the California Consumer Privacy Act (CCPA) is crucial. This regulation mandates the protection of personal information and data privacy. For manufacturers, this means implementing stringent data handling policies to ensure transparency, data security, and accountability in all data practices
OSHA (Occupational Safety and Health Administration)
The Occupational Safety and Health Administration (OSHA) sets and enforces standards that ensure health and safety. Companies must adhere to OSHA’s comprehensive safety protocols to prevent workplace injuries and illnesses.
GMP (Good Manufacturing Practice)
Good Manufacturing Practice (GMP) guidelines are essential in ensuring that products are consistently produced and controlled according to quality standards. Compliance with GMP standards is critical for manufacturers to maintain product integrity and consumer trust, especially in industries like pharmaceuticals, food and beverages.
GDPR (General Data Protection Regulation)
For manufacturers operating in or selling to the European market, the General Data Protection Regulation (GDPR) is a pivotal standard. GDPR demands rigorous data protection, safeguards, and grants individuals greater control over their personal data.
ITAR (International Traffic in Arms Regulations)
The International Traffic in Arms Regulations (ITAR) control the export and import of defense-related articles and services. For defense manufacturing sector, ITAR are mandatory to ensure that military or space-related technologies and data do not fall into the wrong hands. Rigorous control, visitor log and documentation of who accesses this sensitive information are required for the purpose of national security.

How a Visitor Management System Helps Manufacturers Stay Compliant
Plants often have a multitude of rules and regulations to comply with. Here’s how visitor management software helps achieve high compliance:
- Smooth check-ins and consent verification: A VMS can be programmed to request consent for data collection and usage from every visitor. Besides, you can customize sign-in process, aligning it with your corporate requirements.
- Robust data management: Systems securely store and track all visitor data, providing a clear audit trail that can be crucial for compliance with regulations like CCPA and GDPR.
- Pre-visit documentation: The software can automate requests for necessary documents and provide clear instructions. For example, the system can ask to sign legal agreements or a specific NDA before a visitor has arrived, ensuring compliance with ease.
- Tailored visitor experiences: VMS allows for different sign-in processes depending on the type of visitors (e.g., contractors, government inspectors, etc.), which helps in adhering to specific compliance requirements for different groups.
- Safety briefing distribution: For OSHA compliance standards, a VMS can send safety mandatory videos before entrance.
- Audit-ready record keeping: The system maintains backed-up, easily accessible records of all visits, which are invaluable during compliance audits and inspections.
- Real-time alerts and notifications: A VMS can issue real-time alerts to grab immediate attention to potential security breaches.
- Scheduled compliance updates: The software automatically updates compliance procedures and protocols whenever regulatory changes occur, without manual intervention.
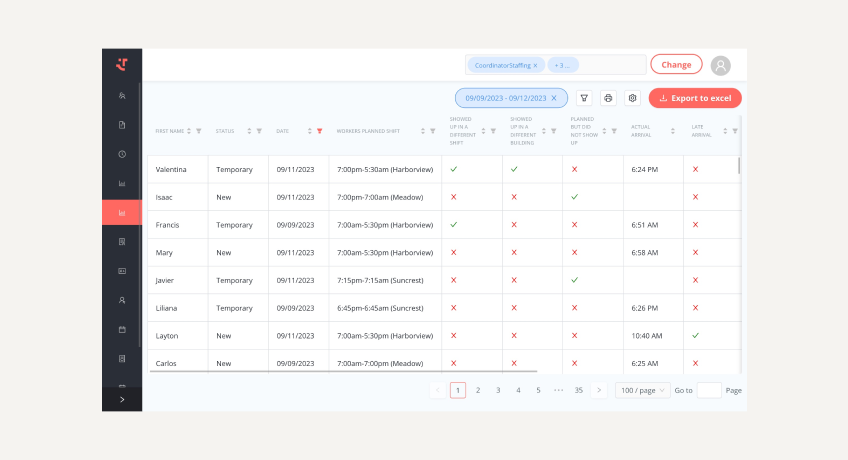
Core Capabilities of a Modern Visitor Management System for Manufacturing
Secure visitor registration and credentialing
This software helps capture important visitor information, scan IDs and capture biometric data where necessary. This first layer of security ensures that only verified individuals can proceed with their visit. This precise control over credentials minimizes security risks and ensures compliance with manufacturing industry standards.
Integrated access control and entry/exit tracking
Integration with existing access control systems is a key feature of modern VMS, enabling seamless control of entry and exit points. The system utilizes a combination of hardware and software to manage visitors, doors, turnstiles, gates, so that the access will be granted only to individuals with valid credentials. Real-time monitoring allows security personnel to immediately address unauthorized access attempts and maintain a secure environment.
Watchlist screening and activity monitoring
Enhancing safety measures, a modern VMS includes watchlist screening functionalities, which automatically cross-reference visitor data with national and international databases to identify potential security threats.
Self-service check-in and badge printing
To streamline the visitor check-in process, many on-premise management systems now offer self-service options that allow visitors to register, submit necessary legal documents and NDAs, and print their badges without assistance. These self-service kiosks can significantly reduce wait times and free up administrative resources from keeping detailed log books manually. Badge printing at the point of entry ensures that all visitors are visibly identified and pre-registered, with badges often featuring the visitor’s name, photo, area of access, and the planned period of time.
Customizable visitor policies and approval workflows
Modern VMS are highly customizable, enabling the creation of specific policies and workflows tailored to different visitor types and security levels required by the company. This level of customization ensures that all compliance requirements are met, without compromising the efficiency of automated processes.
Benefits of Visitor Management Systems in Manufacturing
Physical access control
Modern VMSs are equipped to integrate seamlessly with electronic locking systems, turnstiles, and other physical barriers, ensuring that only approved visitors can enter specific locations within the facility. The system can be programmed to grant access based on various criteria, including the time of day, the visitor’s purpose, and even specific event permissions, thereby creating a secure and controlled environment.
A robust VMS significantly reduces the risk of unauthorized entry by employing advanced verification processes such as biometrics and ID scanning, using PIN codes, or RFID to authenticate the identity of every guest. By ensuring that only verified individuals can access the premises, manufacturing plants can prevent any breaches that might lead to theft, vandalism, or corporate espionage. The presence of a sophisticated visitor management solution itself can act as a deterrent to unauthorized individuals attempting to gain entry into the facility.
Monitoring and logging visitor activity
Monitoring and logging visitor activity are vital functions provided by visitor management software. The system records detailed data on every visitor who enters and exits the facility, including their entry and departure times, the areas they accessed, and their interactions with on-site personnel.
Enabling compliance with security protocols
A visitor management system can help ensure compliance with established regulatory requirements. These systems can be configured to enforce specific measures, such as ensuring that visitors view safety protocols or agree to confidentiality terms before entry.

Evaluating and Implementing the Proper VMS in Manufacturing
Defining visitor policies and approval workflows
Before implementing a visitor management system (VMS) and ditching your old legacy systems, it’s crucial for manufacturing companies to clearly define their visitor policies and approval workflows. Streamlining the workflows in advance ensures that the VMS can be configured to automatically enforce internal or third-party rules, thereby enhancing both security and operational efficiency.
Key system features
By leveraging these features, VMS ensures that manufacturing facilities are secure, compliant, and proficient at preventing breaches:
- Unauthorized entry alerts: Instant notifications for any unauthorized attempts to enter the location ensure immediate response and action at manufacturing plants and sites.
- ID or QR Code scanning: The system can run instant assessments and verify visitor identities through ID or QR code scanning, ensuring accurate and swift processing.
- Geofencing: Real-time evaluations of visitor credentials restrict visitor access to specific areas within the facility.
- Robust registration processes: When choosing a VMS, several key features should be considered to ensure it meets the specific needs of the manufacturing business. The registration process must capture required information and verify identities quickly, creating a smooth first impression for users.
- Badge system: Provides visible identification for visitors across all of your sites, confirming their access rights and enhancing security across all sites.
- Watchlist capabilities: Screens every visitor against known security risks or banned individuals, preventing potential threats.
- Integration with other security systems: Connects with CCTV, access control mechanisms, and other security systems to create a comprehensive security posture.
- Compliance and breach prevention: VMS ensures that manufacturing facilities are not only compliant with stringent security standards but also adept at preventing any breaches.

Training staff and conducting system audits
Once a VMS is selected, thorough safety training for all staff members is essential. Regular refresher courses can help ensure that security staff remain proficient in using the VMS and are aware of any updates or changes to security protocols.
Conducting regular system audits is not a simple and easy way to safety, but it is critical to assess the effectiveness of the VMS. By regularly evaluating the system and staff readiness, manufacturing facilities ensure that their VMS continues to meet all operational and security requirements.